Malware Attack are becoming increasingly sophisticated and include methods of evasion and obfuscation designed to fool users and security administrators who might otherwise be able to spot them. In addition to simple tactics designed to hide the source IP address, polymorphic malware is designed to avoid detection from signature-based detection tools by changing their code. Fileless malware, which does not exist anywhere on the system outside of its RAM, is another example.
Every day we are exposed to many types of malicious software ranging from Malware Attack, Ransomware to spyware.
Types of Malware Attack
Different Types of Malware Attack is as follow:-
1. Computer Viruses
The term virus refers to malware that replicates itself by inserting its code into other computer programs when they are executed. Infected areas are those infected by this replication.
Infecting systems and spreading viruses is accomplished by exploiting vulnerabilities and social engineering. Viruses that evade antivirus software commonly target Microsoft Windows and Mac operating systems.
There are many reasons why viruses are created, malware attack is been done, including profit (such as Ransomware), personal amusement, discovering vulnerabilities and denial of service, sabotage, and experimenting with artificial life.
As a result of viruses, systems fail, resources are wasted, lousy data is corrupted, maintenance costs increase, keystrokes are logged and personal information is stolen (for example, credit card numbers).
2. Computer Worm
A computer worm is a self-replicating malware program that replicates itself on infected computers in order to spread to other computers.
Wms often use computer networks to spread, exploiting security flaws on target computers. Even consuming bandwidth is usually enough to harm a network caused by worms. Conversely, a virus almost always corrupts or modifies files on a victim’s computer.
An example of a ransomware crypto worm is WannaCry, which exploited the EternalBlue vulnerability without user interaction.
While many worms are designed to spread and not change the systems they pass through, even payload-free worms can cause significant disruptions. The Morris worm and Mydoom caused major disruptions by increasing network traffic despite their benign nature.
3. Trojan Horse
Malware Attack that disguises itself as a legitimate program is referred to as a trojan horse or trojan. Trojan Horse refers to the deceptive Trojan Horse that led to Troy’s fall in Ancient Greek mythology.
Social engineering techniques, such as phishing, are commonly used to spread Trojans. Email attachments disguised to look genuine (e.g. Excel spreadsheets) may be tricked into executing them. The trojan is installed after the executable file has been opened.
While trojans can have a variety of payloads, most act as backdoors that give attackers unauthorized access to infected computers, PII, bank login credentials, passwords and internet activity can be accessed by Trojans. Trojans are also used to carry out ransomware attacks.
Trojans are different from computer viruses and worms in that they generally do not try to infect or propagate themselves.

4. Rootkits
Rootkits are collections of malware that allow unauthorized access to a computer or areas of its software. They often mask their presence or that of other programs on the system. Attackers can automate the installation of rootkits or install them with administrator access.
Phishing or exploiting vulnerabilities are direct attacks on systems that can provide access.
It is challenging to detect rootkits because they can subvert antivirus programs designed to detect them. There are many ways to detect malware, including using trusted operating systems, behaviours, signatures, differences, and memory dumps.
Rootkit removal can be difficult or impossible when rootkits reside in the kernel. It may be necessary to replace hardware or use specialized equipment to remove firmware rootkits.
5. WordPress Malware Attack
A malware infection occurs when malicious software exploits a site’s weaknesses to carry out harmful activities. When a WordPress site is infected with malware attack, it can adversely affect its performance at every level, from the server to the user experience to its SEO rankings. You might be unable to save your website by the time you realize what is happening to it if you don’t pay attention now.
The security of WordPress is a serious matter. Through cross-site contamination, WordPress’ architecture has been exploited to compromise servers. The extensibility of WordPress makes it more vulnerable; plugins and themes can contain loopholes, Easter eggs, backdoors, and a wide range of other issues. Finding out you’re selling Viagra or supporting a random cause on your computer can be devastating.
There are several known security issues in WordPress’ core, which are quickly addressed by the WordPress team to protect the millions of website owners who use and depend on the software. To protect your website from such harmful attack and security issues, One must have the hired the expert for the WordPress Malware Removal Service. Search Combat assures you with the best WordPress Malware Removal Service and make your website secured from harmful attacker.
6. Malicious Redirects
A WordPress website may be redirected to spam or scam websites if redirector malware modifies the site/home URL settings. Using this technique, hackers scam website visitors and capitalize on the existing traffic. Troubleshooting some variations can be particularly challenging because they only redirect a unique visitor once.
As it only occurs once for a visitor in a specific browser session, it becomes tough for the website administrator to track down and isolate. In most cases, redirect-based malware is caused by unpatched or outdated plugins and themes. There may be more malware hidden within the website than just redirection.
7. Phishing
Phishing campaigns aim to trick victims into providing sensitive personal information, login credentials, or credit card and payment transaction information. Phishing campaigns often use legitimate brands. Attackers often create a sophisticated page to mimic an authentic website. Phishing pages are dangerous and should be avoided at all costs. Search authorities like Google or Bing will quickly blocklist any websites hosting phishing content if they detect phishing on a website. A website’s reputation can ultimately be damaged, and revenue negatively affected. This is especially true if the website is an e-commerce site.
8. Backdoors
As their name implies, backdoors work precisely as they are supposed to. Attackers use this malware to conceal themselves from website owners by creating a backdoor entry. Approximately 60.04% of infected websites had at least one backdoor last year alone, according to our latest Website Threat Research Report for 2021. Backdoors are essential to hackers, as evidenced by this example. Attackers typically infect websites once they discover unpatched vulnerabilities, insecure admin panels, or reused passwords. Even with all the vulnerabilities on the system patched, the backdoor allows unauthorized access to the website.
Backdoors of all shapes and sizes can damage websites in various ways.
9. Spam Content
The most common infection on hacked websites is SEO spam, also known as search engine spam or spamdexing. Attackers aim to manipulate search engine results by using a website’s web pages and rankings to promote their shady services. Since these infections are typically well-disguised and challenging to detect, they can be a nightmare for web admins.
10. Ransomware
The purpose of Ransomware is to prevent access to a computer system or data until a ransom is paid. In addition to phishing emails and Malvertising, infected websites and exploiting vulnerabilities are all ways Ransomware spreads.
There is a risk of data breaches, leaks, intellectual property theft, and downtime caused by ransomware attacks.
It is common for ransom payments to range from a few hundred dollars to hundreds of thousands of dollars. Bitcoin and other cryptocurrencies are accepted.
11. Keylogger
As the name implies, keyloggers are malicious programs that record each keystroke typed on a particular computer’s keyboard and monitor and store them. As well as smartphones and keyloggers can also be installed on laptops and tablets.
When it collects information, a keylogger sends it to the attacker, who can then extract sensitive information like login credentials and credit card numbers.
12. Grayware
It’s a term that describes non-malware programs or files that slow down the computer and pose a security risk. Grayware was coined in September 2004.
Generally, grayware behaves in an annoying or unwelcome manner, at the very least. At worst, grayware monitors the system and sends home information about it.
Adware and spyware are both examples of grayware. In contrast, most antivirus programs are capable of detecting potentially unwanted programs and offering to remove them as soon as they are detected.
It is usually easy to remove adware and spyware from a computer because they do not have the same malicious intent as other types of malware.
There is a more significant concern when it comes to the mechanism used by grayware to gain access to the computer, whether it is social engineering, unpatched software, or another vulnerability. The same method can be used by other malware, such as Ransomware, to gain access to your system.
In the presence of adware, an alert can be sent to the user or device to warn them of an issue that will need to be corrected.
13. Fileless Malware
To infect a computer with fileless malware, legitimate programs are typically used to facilitate infection. Unlike other malware infections, it does not rely on files and leaves no footprint, making it challenging for anti-malware software to detect and remove. Memory-based artifacts, such as RAM, exist exclusively on computers.
There is no doubt that fileless malware has been around for quite some time, but it has only gained mainstream recognition in 2017. In the early days of fileless malware attack, Frodo, Number of the Beast, and the Dark Avenger were all used. A fileless malware attack has been perpetrated on the Democratic National Committee and Equifax in the recent past.
It is immune to anti-computer forensic strategies, including safe listing, signature detection, hardware verification, pattern analysis, and time-stamping, since fileless malware leaves no trace on the computer’s hard drive.
Investigators using digital forensics to identify unlawful activities are left with very little evidence. However, since it is designed to operate in memory, it generally lasts for only a short time before being destroyed by a reboot.
14. Adware
The term “adware” refers to a type of grayware designed to display advertising on your computer screen, usually in the form of a pop-up or a web browser.
You are typically tricked into installing it on your computer, tablet, or smartphone by the appearance of it being legitimate or piggybacking on another program so that it appears legitimate.
As one of the most profitable and least harmful types of malware on mobile devices, adware has become one of the most prevalent forms of malware. There are several ways in which adware generates revenue by continuously displaying advertisements to the software user.
15. Malvertising
In simple terms, Malvertising may be defined as advertising to spread malware through a combination of advertising and malicious code. There are several ways to accomplish this, but the most common method involves injecting malicious or malware-laden advertisements into legitimate advertising networks and websites.
There is no doubt that advertising is one of the best ways to spread malware because a lot of effort is invested in creating advertisements to attract users’ attention and sell or advertise a product.
It is also important to note that Malvertising also benefits from the reputation of the sites in which it is placed, such as reputable and high-profile news websites.
16. Spyware
In the field of malware attack, spyware is a piece of software that gathers information about people and organizations, sometimes without their awareness. It sends the collected information to the attacker without the victim’s consent.
There are several ways in which spyware can be used intentionally to track and sell your internet usage data, capture your credit card or bank account information, or steal personally identifiable information (PII).
As a result of some types of spyware, additional software may be installed on your device, and settings may be changed. Since spyware does not present as much of a threat as other types of malware, it is usually simple to remove.
How Does Malware Spread?
There are standard ways that malware spreads:
- Software security vulnerabilities can be exploited by malware to gain unauthorized access to computers, hardware, or networks due to those defects.
- Software, hardware, networks, or systems compromised by unintended or intended backdoors are called backdoors.
- There is a phenomenon known as drive-by downloads, the unintended downloading of software with or without the user’s knowledge.
- Having a homogeneous network and running the same operating system on all computers increases the chances of a successful worm spreading to other computers if they run the same operating system and are connected to the same network.
- As the name suggests, privilege escalation refers to the process in which an attacker is granted elevated access to a computer or network and then uses that access to launch an attack on that system.
- Often difficult to detect and stop because of their ability to exploit various vulnerabilities, blended threats tend to be malware packages combining characteristics from different types of malware.
5 Distribution Stages of Malware Attack
Search Combat Experts explain what happens during a typical malware attack stage. The attack starts with the initial infection, where the attacker sends a malicious file to the victim via email, instant messaging, social media platforms, etc. Once the victim opens the attachment, it begins installing itself onto its computer without consent. After installation, the malware performs several actions, such as encrypting files, changing system settings, monitoring keystrokes, sending spam emails, etc.
Next, the malware moves into the distribution stages, which are given below:-
Stage 1: Entry
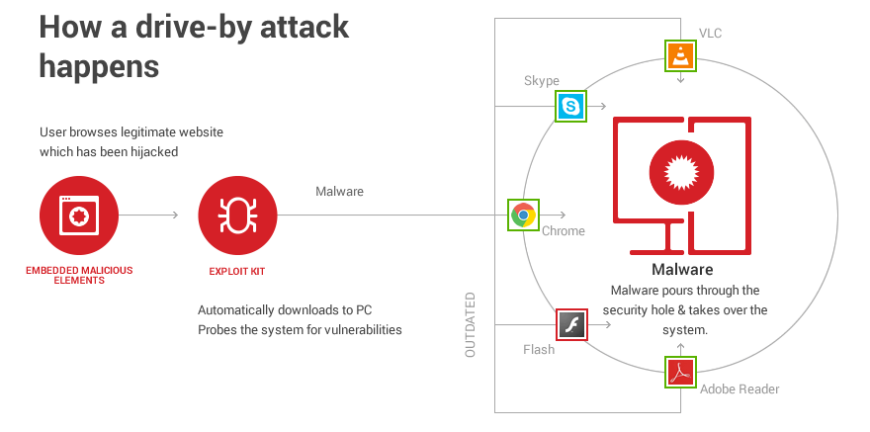
This first phase of malware attack involves a drive-by download from an entry point, such as a hijacked website or an email that contains a malicious link.
Drive-by downloads
Drive-by downloads can be defined as the act of downloading malicious web code by accident simply by visiting a web page and then visiting that page again.
In a drive-by download, the user does not know that the download is taking place and occurs automatically. There are several different types of drive-by downloads. Still, one of the most common types involves malicious JavaScript injected into legitimate web content to redirect the browser to further malicious web content. Moreover, this sophisticated JavaScript can be hidden by obfuscation (in other words, making them unreadable) and polymorphism (meaning that the code changes based on your view). As a result, traditional antivirus solutions based on signatures won’t be able to detect this type of tricky code.
Stage 2: Traffic Distribution
Cybercriminals are being offered a new traffic distribution system on darknet marketplaces that assists them in directing users to sites hosting exploit kits and conducting web-based malware attack by directing them to these sites. The unsuspecting user is redirected to an exploit kit once a drive-by download reaches their browser and a drive-by download has reached browser. In contrast, elaborate traffic distribution systems (TDS), on the other hand, create multiple redirection paths that are nearly impossible to trace and, therefore, cannot be blocked instead of sending users to known exploit kit hosting sites.
It is important to note that some legitimate TDS systems are out there, such as those used for advertising and referral networks. Like any other software, legitimate TDS solutions can be hacked and exploited to drive traffic to malware-hosting sites instead of benign ones. Still, just as any other software, they are vulnerable to being hacked.
The criminals are using a TDS called Sutra to manage traffic from drive-by downloads based on the IP geolocation, operating system, browser, or any other information that can increase the chances of getting infected with malware. Using the latest version of Sutra TDS 3.4, hackers can buy the latest version for just $100, which allows them to generate more than a million clicks per hour on a low-end server.
TDS networks often filter traffic to keep their sites hidden from search engines and security companies. As well as this, they use fast-flux networks to continuously cycle thousands of IP addresses through DNS records and prevent their malware-hosting sites from being blocked.
Stage 3: Exploit
The next step in a modern web attack is downloading an exploit pack from the malware-hosting site. During this phase of a web attack, the actual exploit for a browser is downloaded, usually from the website that is being used to host the malware to carry out the attack. Many exploits are executed using these kits to exploit vulnerabilities in web browsers and plugins such as Flash, Silverlight, and Java associated with these browsers.
This is the part of the web attack where the actual exploit for a browser is downloaded, usually from the website used to host the malware so that the actual attack can be carried out based on the exploit.
These vulnerabilities will likely be based on information from the user’s browser, such as information extracted from their user agent. In this case, you may not have installed the latest Flash updates, which results in the Flash plugin in your browser being vulnerable, allowing the exploit kit to gain access to your system without the user being aware of it.
Stage 4: Infection
Once an attacker has exploited a vulnerability in an application to gain some control over the computer, the next step in the attack is to download a malicious payload that will infect the system with the malicious payload. As the name implies, the payload is the malware or virus that will be used to steal data from the user or extort money from them.
There is a wide variety of infectious payloads available to the hacker they can choose from. Several different types of payloads are commonly used in the modern day.
System Exploit
When a malicious software, chunks of data, or sequences of commands (such as software, data, or commands) exploit a bug, glitch, or vulnerability in a service, host, server, network, or more complicated system, it allows unauthorized access, unauthorized privilege escalation, data disclosure, or denial-of-service to be performed.
End-user engagement is not required for system exploits. The attacker may tempt the end-user, such as phishing emails or web links, to click on URL links or buttons to execute a malicious piece of code. ShellShock was an example of an attacker using sophisticated code to target vulnerabilities directly.
The attackers aim to take over a victim’s browser, host, service, or network at this stage. Their malicious materials are generally short and intelligent, containing only enough content to accomplish the exploit. They use other dedicated materials to execute malicious activities once the system has been exploited.
Stage 5: Final Execution of Website Malware Attack
During the final phase of an attack, the malware begins to carry out the malicious activities it has been programmed to carry out the attack. It can be seen in the screenshot below that the Ransomware is communicating the status of its infection back to its command & control host using POST requests. A Ransomware attack will encrypt the victim’s files and then ask the victim for payment for a decryption key to enable them to recover their files.
In addition to stealing confidential data such as usernames and passwords, other malware may also gain access to financial data (online banking credentials, credit card details, etc.) or may provide the attacker with a foothold within an organization to enable further lateral movement to specific data within the organization.
CONCLUSION
Malware attack are becoming increasingly sophisticated. New variants are being developed every day. As a result, you must put measures in place to protect yourself from Ransomware. This includes having a plan to recover data once a ransom demand is received. In addition, you must ensure that you have adequate backups and regularly test those backups. Finally, you must develop a strategy to prevent future infections.










